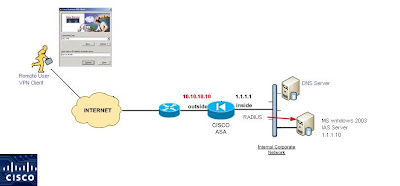
Hi Guys Today we are going to discuss how to setup Remote access
VPN connection between Remote Clients / Mobile Users / Cisco VPN
Clients ... (its same names) and ASA 5500 by authenticating Users
Against Active directory using MS 2003 IAS server (which is MS
RADIUS server)
VPN connection between Remote Clients / Mobile Users / Cisco VPN
Clients ... (its same names) and ASA 5500 by authenticating Users
Against Active directory using MS 2003 IAS server (which is MS
RADIUS server)
IPSEC is configured in this example with these considerations
Cryptomap is applied on outside interface of ASA Appliance
Xauth (extended Authentication) of VPN clients will be happening against RADIUS (which would be ISA server Windows 2003)
DNS (1.1.1.11) and Windows 2003 IAS server (1.1.1.10) is sitting Inside
Here we go
interface Ethernet0
nameif outside
security-level 0
ip address 10.10.10.10 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 1.1.1.1 255.255.255.0
name-server 1.1.1.11
domain-name itpeoplerworld.com
#Create pool of Addresses for assignment of ip addresses
dynamically to remote VPN clients
ip local pool vpnclient 1.1.1.200-1.1.1.250
Nat (inside) 1 0.0.0.0 0.0.0.0
Global (ouside) x.y.z.a (
This depends upon your scenario)
# Appropriate Route inside and Route outside statements depending
upon the network Layout.
# Now create AAA server group named "VPN" and mention RADIUS and
add MS 20003 IAS server as a member of this "VPN" group and mention
Security Key as well which is "Cisco" in our case
aaa-server vpn protocol radius
aaa-server vpn host 1.1.1.10
key cisco
#Now create VPN user policy and specify DNS IP address and domain
name
group-policy VPNPOLICY internal
group-policy VPNPOLICY attributes
dns-server vlaue 1.1.1.11
default-domain value itpeopleworld.com
# As specif VPN config PHASE 2 Configuration mentioning Encryption
type , Hash Algorithm
crypto ipsec transform-set myset esp-des esp-md5-hmac
# Dynamic Crypto map
crypto dynamic-map mydmap 10 set transform-set myset
# Enable RRI (reverse routre injection)
crypto dynamic-map mydmap 10 set reverse-route
# Binding map to ISAKMP
crypto map maymap 10 ipsec-isakmp dynamic mydmap
# Now specifying Interface to whihc cryptomap is attached to
Crypto map mymap interface outside
# ISAKMP PHASE 1 config is as under
isakmp enable outside
isakmp policy 10 authentication pre-share
isakmp policy 10 encryption des
isakmp policy 10 hash md5
isakmp policy 10 group 2
isakmp policy 10 lifetime 1000
#Create a new tunnel Group as Security appliance provides default
tunnel group for remote access whihc is (defaultRAGroup) but here
we will use our own group
tunnel-group mygroup general-attributes
address-pool vpnclient
authentication-server-group vpn (remember be case sensitive)
default-group-policy VPNPOLICY
# Enter Preshare key to configure authetication poilyc
tunnel-group mygroup ipsec-attributes
preshare key xyz
**********************************
Now Go on VPN client appliaction
start > Program> Cisco VPN client
click New to create new Connection
Under host give outside interface ip address whihc is 10.10.10.10
in our case
Under authentication tab , Select group authentication radio button
Name = mygroup
password =xyz
Thats It and now you need to connect and it will ask for One more
Username and password whihc would be your IAS MS windows 2003
Server has in it
Microsoft Windows 2003 Server with IAS Configuration
Complete these steps to configure the Microsoft Windows 2003 server
with IAS.
first you need to install IAS server from Control panel and ADD/
Remove Program
Select Administrative Tools > Internet Authentication Service now
right click on RADIUS Client to add a new RADIUS client.
Give name
Standard, and shared secret is Cisco.
Go to Remote Access Policies, R.C (right click) on Connections to
Other Access Servers, and select Properties.Endure Grant Remote
Access Permissions is selected.
Click Edit Profile and check
under Authentication tab, check Unencrypted authentication (PAP,
SPAP), MS-CHAP, and MS-CHAP-v2.
under Encryption tab, ensure that the option for No Encryption is
selected.
Go in Administrative Tools > Computer Management > System Tools >
Local Users and Groups, R.C on Users and select New Users to add a
user into the local computer account.
I hope I don’t need to mention how to create a user .... If you feel
that you need this type of help ...... then go to Learn windows for
extreme Dumps’.com .. thanks For visiting ...
One thing i would suggest to check On Users screen under General
tab, ensure that the option for Password Never Expired is selected
Under Dial-in tab, select the option for Allow access
Here is one way to test either ASA is communicating with IAS Server
or not
test aaa authentication radius host 10.1.1.10
It will ask for username and password ..... give username and password that you just created on IAS server
And one last thing
dont forget
Debug Crypto ISAKMP
For troubleshooting

No comments:
Post a Comment